11+ pages which of the following are methods for providing centralized authentication 725kb. Type 1A STP or Category 5 UTP TACACS RADIUS A false server intercepts communications from a client by impersonating the intended server. Select two Select two RADIUS. Students who viewed this also studied. Check also: methods and understand more manual guide in which of the following are methods for providing centralized authentication Which of the following are methods for providing centralized authentication authorization and accounting for remote access.
Select two 8021x EAP PKI TACACS RADIUS AAA. 8021X authentication 8021X is a method for authenticating the identity of a user before providing network access to the user.

Authorization Services Guide
| Title: Authorization Services Guide |
| Format: PDF |
| Number of Pages: 239 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: December 2020 |
| File Size: 2.6mb |
| Read Authorization Services Guide |
 |
For authentication purpose the wireless client can associate to a network access server NAS or RADIUS client such as.
You want to implement RADIUS to centralize remote access authentication and authorization. Which of the following. 1145 Practice Questions 1 Which of the following are methods for providing. You have decided to implement a remote access solution that uses multiple remote access servers. Pages 798 Ratings 100 3 3 out of 3 people found this document helpful. Select two TACACS AAA EAP 8021x PKI RADIUS.

Oauth2 Introduction Through Flow Diagrams In 5 Minutes Oauth Io Blog Coding Secret Notes Access Token
| Title: Oauth2 Introduction Through Flow Diagrams In 5 Minutes Oauth Io Blog Coding Secret Notes Access Token |
| Format: PDF |
| Number of Pages: 318 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: February 2018 |
| File Size: 800kb |
| Read Oauth2 Introduction Through Flow Diagrams In 5 Minutes Oauth Io Blog Coding Secret Notes Access Token |
 |

Java Ee Front Controller Design Pattern Introduction Controller Design Design Pattern Java Software Design Patterns
| Title: Java Ee Front Controller Design Pattern Introduction Controller Design Design Pattern Java Software Design Patterns |
| Format: ePub Book |
| Number of Pages: 336 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: April 2018 |
| File Size: 2.8mb |
| Read Java Ee Front Controller Design Pattern Introduction Controller Design Design Pattern Java Software Design Patterns |
 |

Identify Authenticate Authorize The Three Key Steps In Access Security Wallix
| Title: Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
| Format: eBook |
| Number of Pages: 158 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: February 2020 |
| File Size: 1.3mb |
| Read Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
 |

Imagine How Any Centralized Anization Works There Are People Responsible For The Adoption Of Strategic And Vital Dec No Response Accounting Payment Gateway
| Title: Imagine How Any Centralized Anization Works There Are People Responsible For The Adoption Of Strategic And Vital Dec No Response Accounting Payment Gateway |
| Format: eBook |
| Number of Pages: 304 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: July 2021 |
| File Size: 3mb |
| Read Imagine How Any Centralized Anization Works There Are People Responsible For The Adoption Of Strategic And Vital Dec No Response Accounting Payment Gateway |
 |

Peap And Eap Tls On Server 2008 And Cisco Wlc Eap Server Windows Server
| Title: Peap And Eap Tls On Server 2008 And Cisco Wlc Eap Server Windows Server |
| Format: eBook |
| Number of Pages: 160 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: March 2017 |
| File Size: 1.1mb |
| Read Peap And Eap Tls On Server 2008 And Cisco Wlc Eap Server Windows Server |
 |

The Service Locator Design Pattern Is Used When We Want To Locate Various Services Using Jndi Lookup Considering Design Patterns In Java Pattern Design Design
| Title: The Service Locator Design Pattern Is Used When We Want To Locate Various Services Using Jndi Lookup Considering Design Patterns In Java Pattern Design Design |
| Format: ePub Book |
| Number of Pages: 169 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: July 2020 |
| File Size: 5mb |
| Read The Service Locator Design Pattern Is Used When We Want To Locate Various Services Using Jndi Lookup Considering Design Patterns In Java Pattern Design Design |
 |

Paring Proof Algorithms Proof Of Work Vs Proof Of Stake Infographic Holytransaction Algorithm Stakes Infographic
| Title: Paring Proof Algorithms Proof Of Work Vs Proof Of Stake Infographic Holytransaction Algorithm Stakes Infographic |
| Format: eBook |
| Number of Pages: 134 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: September 2020 |
| File Size: 3mb |
| Read Paring Proof Algorithms Proof Of Work Vs Proof Of Stake Infographic Holytransaction Algorithm Stakes Infographic |
 |

Identify Authenticate Authorize The Three Key Steps In Access Security Wallix
| Title: Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
| Format: ePub Book |
| Number of Pages: 299 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: February 2017 |
| File Size: 725kb |
| Read Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
 |

Advantages Disadvantages Of Iaas Explained Cloud Puting Services Technology Infrastructure Cloud Puting
| Title: Advantages Disadvantages Of Iaas Explained Cloud Puting Services Technology Infrastructure Cloud Puting |
| Format: eBook |
| Number of Pages: 226 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: August 2021 |
| File Size: 5mb |
| Read Advantages Disadvantages Of Iaas Explained Cloud Puting Services Technology Infrastructure Cloud Puting |
 |

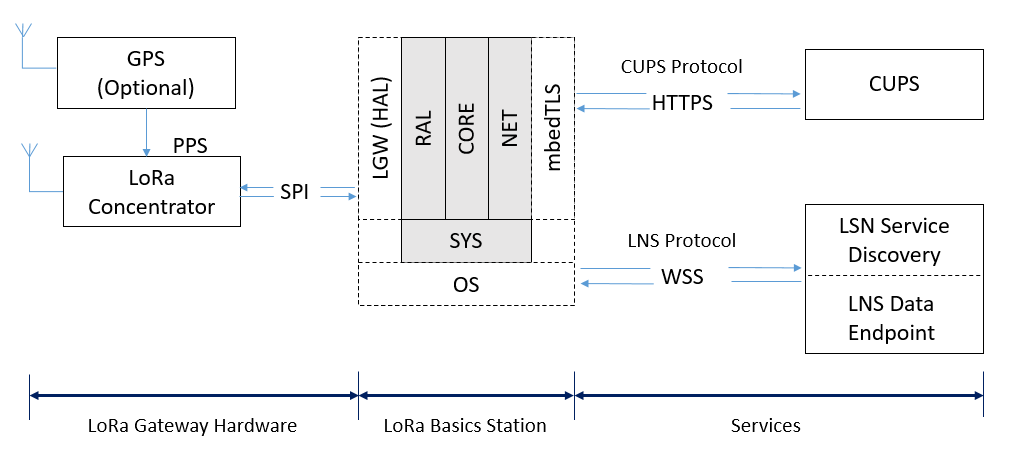
How To Use Lora Basics Station Developer Portal
| Title: How To Use Lora Basics Station Developer Portal |
| Format: PDF |
| Number of Pages: 166 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: May 2020 |
| File Size: 2.8mb |
| Read How To Use Lora Basics Station Developer Portal |
 |

How Does Single Sign On Sso Work Onelogin
| Title: How Does Single Sign On Sso Work Onelogin |
| Format: eBook |
| Number of Pages: 260 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: January 2018 |
| File Size: 2.3mb |
| Read How Does Single Sign On Sso Work Onelogin |
 |
You have decided to implement a remote access solution that uses multiple remote access servers. Which of the following applications typically use 8021x authentication. RADIUS supports more protocols than TACACS.
Here is all you need to learn about which of the following are methods for providing centralized authentication Get the detailed answer. You want to implement RADIUS to centralize remote access authentication and authorization. Which of the following are methods for providing centralized authentication authorization and accounting for remote access. Java ee front controller design pattern introduction controller design design pattern java software design patterns identify authenticate authorize the three key steps in access security wallix the service locator design pattern is used when we want to locate various services using jndi lookup considering design patterns in java pattern design design how to use lora basics station developer portal peap and eap tls on server 2008 and cisco wlc eap server windows server imagine how any centralized anization works there are people responsible for the adoption of strategic and vital dec no response accounting payment gateway RADIUS supports more protocols than TACACS.